In my previous post, I teased that I’d started recording commercial audiobooks through Audible’s ACX marketplace in 2025. I’m thrilled to announce the first significant publication from this project: the audiobook edition of The Horror Writer: A Study of Craft and Identity in the Horror Genre.
Compiled and edited by Joe Mynhardt—and narrated by yours truly—this book collects 26 essays from just as many different professional horror authors about the craft of writing, pitching, and publishing genre fiction in today’s marketplace:
The Horror Writer covers how to connect with your market and carve out a sustainable niche in the independent horror genre, how to tackle the writer’s ever-lurking nemesis of productivity, writing good horror stories with powerful, effective scenes, realistic, flowing dialogue and relatable characters without resorting to clichéd jump scares and well-worn gimmicks. Also covered is the delicate subject of handling rejection with good grace, and how to use those inevitable “not quite the right fit for us at this time” letters as an opportunity to hone your craft.
Plus… perceptive interviews to provide an intimate peek into the psyche of the horror author and the challenges they work through to bring their nefarious ideas to the page.
This is the third audiobook I have delivered through ACX, and the first one that feels worth sharing. I’m really proud of how this came out, and extend my thanks to HellBound Books, and in particular to Xtina Marie for her editorial direction of this project. Xtina encouraged my efforts to find and apply a unique tone to each essay in this collection, reflecting how each came from a different writer’s hand. I loved the challenge this brought to narrating this book, and learned so much about the range of my own voice in the process. I humbly hope that you’ll enjoy listening to the results.
For more information and a free audio sample, check out the book’s page on Audible. And if you’re a reviewer of either horror fiction or non-fiction about writing and would like a promo code, feel free to drop me a line!
Well, I had a fairly productive year in the realm of small-stakes media. I got to guest twice on one of my favorite long-running game podcasts, and produced six more episodes of my own show. I also invested significant time into new audio production skills, though I don’t have much to show for it just yet. And I waded around a bit with freelance article writing for the first time in many years.
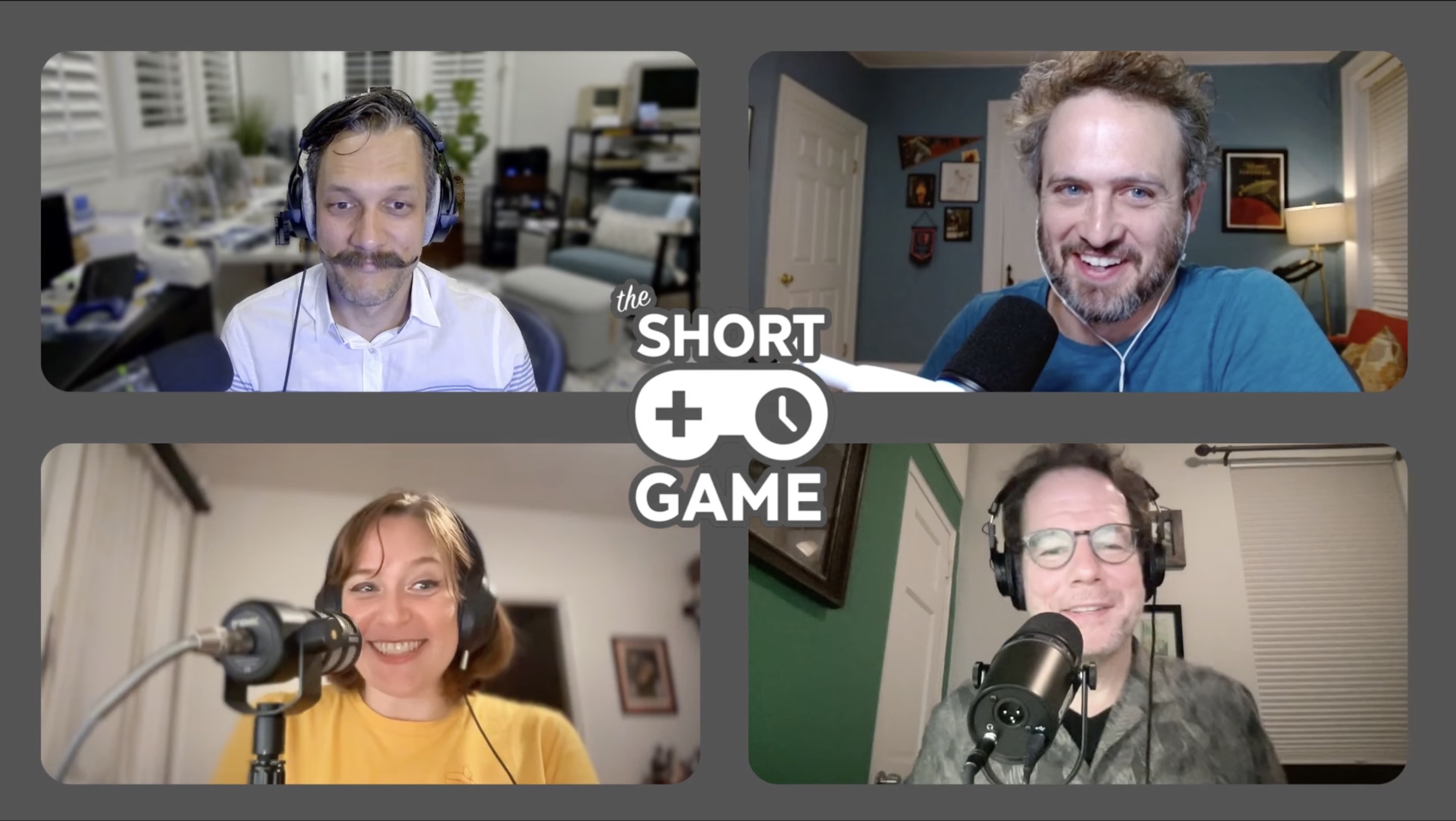
The Short Game
I guested on two episodes of The Short Game:
Episode 430, a general chat about the Steam Deck game console, for which I am known to have a certain affinity. (Also on YouTube.)
Episode 443, discussing fan-made remakes and remixes of older commercial games that are playable on the Steam Deck. (Also on YouTube, or you can just skip to my cat interrupting us.)
The Short Game has been one of my favorite podcasts for some ten years now, ever since they started covering IFComp, during the brief window I was in charge of that annual competition. It’s literally the only game-related media I have consistently followed over this whole span. The chance to be a part of it like this—twice!—was an absolute delight. The show just today returned to the air after a half-year hiatus, and I hope I can revisit its virtual studios soon.
Venthuffer
I recorded another six-episode season of Venthuffer, my strictly-audio-only podcast that was originally about the Steam Deck, but clearly wanted to be more about video games in general, or even just topics tangential to the way that I approach video games. I count the final two episodes—a profile of game auteur Jeff Minter, and a genealogical dive into “Halstrick”, my chosen gaming handle—among the best self-contained works of audible media that I have ever made.
I really do want to get back to Venthuffer, and I even know what I’d like to record next. However, an unexpected late-summer opportunity temporarily redirected my energy and attention for audio production into another outlet, as follows.
Audiobooks
I’ve long been interested in developing more audio narration skills, particularly with audiobooks. After serendipitously gaining a new mentor in this field in August, I spent the final third of the year pouring much of my attention into audiobook production, by way of ACX. From September through December, I recorded the following, each after a successful ACX audition:
A very short self-help book.
Another short book about generative AI, which I didn’t realize was itself absolutely AI-generated until halfway into the project.
An anthology of two dozen essays from professional horror-genre authors, sharing stories and advice on the craft of writing fiction, and the science of selling it.
The first two audiobooks have now been published—the second under a pseudonym—but I’ve chalked them up as educational experiences that I need not name, let alone link to. They have each sold one or two copies, and I’m fine with that.
The third audiobook is still under review by its rights-holder, so I can’t name it yet either. But I do very much hope for its publication early in the new year. When that happens, I plan to share far and wide. It’s gonna be a good one.
Linux Magazine and LWN.net
I had three paid articles published in Linux Magazine, which has kindly allowed me to host and share PDFs of them:
A profile of the Steam Deck from the perspective of a Linux user curious about exploring the machine’s open-source underpinnings, using only the software and services that the game console ships with.
A guide to finding, installing, and using “mods”—fan-made software that modifies the behavior of commercial games—on your Steam Deck.
A high-level overview of creating parser-based interactive fiction games using Inform on Linux.
I also wrote one article for LWN.net about Memcached.
I enjoyed working with both of these publications. My time and attention for this sort of writing got absorbed by job hunting and then BumpySkies in the latter part of 2025. I look forward to writing more articles about doing interesting things with Linux, once I have enough attention freed up for it.
To that end, I intend to be kind to my attention span in 2026—which is to say, I intend to meter it out with fiercely guarded care, so that I can keep working with brilliant people to put small and interesting things out into the world. May the new year bring you, too, enough of a peaceful reset to let your attention remain sovereign.

In October of 2025 I resumed active development of BumpySkies, a free turbulence forecaster for passenger flights over the continental United States. This happened almost exactly six years after I wrote a Fogknife post titled BumpySkies is my masterpiece, alas, where I acknowledged the site as the pinnacle of my personal software-development achievement, and stated that I had no plans to develop it any further. True enough, at the time, and for quite a while after! But this past fall, I found myself inspired to pick it back up anyway, seeing the project with fresh eyes, and bringing new development tools to bear on it. I feel enormously grateful to have the project back on my bench, once again deeply aware of how it works—and with new knowledge of how many people it helps.
Rather than respond point-by-point to all the objections that I had raised in 2019, let me relate how, this past October, I happened to look at a Google Analytics page that I had set up on a whim a couple of years earlier, and noticed that about 8,000 individuals per month were visiting BumpySkies. (AKA “8K MAU”.) That’s not a quit-your-day-job-right-now number, but it’s absolutely a hey-um-a-lot-of-people-are-actually-using-this number. Other statistics showed that most of these 8,000 actually actually used the site as intended: they performed at least one forecast lookup, and then lingered at least a minute or two while they took in the information.
When I wrote that post in 2019, I doubted that BumpySkies would survive the first Trump administration. At the start of 2025, I assumed it wouldn’t survive the first few months of Trump II. I was, happily, wrong on both predictions. Perhaps BumpySkies will run out of luck some day, its federal data sources defunded and silenced by a science-hostile government. But until then, the site undeniably serves thousands of my fellow nervous flyers every month, far more than I would have guessed.
Between jobs and hungry for something meaningful to work on, I couldn’t deny the call. I waded back in, this time swathed in the strange energies of AI-collaborative engineering that simply didn’t exist in 2019. Here is a high-level catalog of what I’ve accomplished over the last two months:
Updated the server’s OS from Debian 9, which was on its very last legs of community support, to Debian 12.
Checked the code into literally any kind of version control.
Set up a development environment separate from the production server, including a “development mode” that lets me work against a fixed flight-and-weather data set instead of relying only on live data streams.
Established proper activity logs and other table-stakes metrics to keep me informed on whether BumpySkies is actually working like it’s supposed to.
Fixed bugs that I’ve known about for years, but which were too hard to work on, because there was no version control, development environment, or logging.
Re-established communication with my contacts at NOAA and FAA, and introduced myself to new contacts as needed.
Caught up on the current status and future roadmaps of the U.S. government data sources that BumpySkies uses, and made my own plans and timelines to match.
Launched a BumpySkies newsletter, now three issues in.
Opened the first BumpySkies user survey, which has collected dozens of excellent notes.
Expanded support for Canadian, Mexican, and Central American airlines.
Set up a bug-reporting button, which generates one or two reports per day—just enough for me to stay on top of, and personally thank people for.
Started to plan some major new features and improvements for the coming year, the specifics of which are to be informed by the results of the survey, as well as active queries and applications I have regarding further data resources.
And, yes, I am using generative AI tools: Claude.AI for assistance with research and data analysis, and a Claude Code as a programming collaborator. My methods for working with these tools are informed and inspired by an April episode of The Talk Show podcast, where Craig Mod describes how he built a personal project of his own—a tiny, purpose-built, limited-membership social network—over the course of weeks. Mod worked carefully and deliberately with Claude Code to plan and build each part of the system, which included personally reading and comprehending all of the coding bot’s proposed changes, and never hesitating to question the work or suggest alternative approaches. In the end, Mod had a sophisticated piece of software whose internal operation he knew intimately well, but whose rapid iterative development was enabled largely by generative AI. On the podcast, Mod said that he could have built the whole thing from scratch, sure, but he probably wouldn’t have.
And so it is with me and this new phase of BumpySkies. I don’t consider my approach “vibe coding”. I think I did “vibe code” some sloppy software earlier in my AI experiments, and it felt awful: in every case I ended up with a pretty web app that fulfilled the bullet list of things I had asked for—but I had no idea how it worked, and so I had little motivation to make it work better. The result always felt plasticky and lifeless. My new BumpySkies work feels very, very different. I feel complete ownership of everything I change, whether or not an AI tool assists with it. I recognize AI as a mirror with no mind, a window into a vastness of muddled human knowledge which isn’t intelligent alone but which can be applied—with care, judgment, and attention—to intelligent purposes, ones that reflect and extend a creator’s taste.
And I have found my taste again, when it comes to where I want to see BumpySkies go next. If there’s one thing I’m looking forward to in 2026, it’s continuing to work with BumpySkies—my living masterpiece—to bring it the attention and growth that it deserves.

This post contains a mild and anonymized spoiler for “Rosewater”.
I had a great time playing Control on Saturday night. On learning from friends that a sequel was recently announced, I resolved to give the game one more try, picking up where I last left off several months ago. Control has long floated near the top of my list of single-player, narrative-rich video games that I’ve long felt pretty bad about not finishing, alongside Elden Ring, Outer Wilds, and many other titles that are near-universally beloved by both trusted friends and the world’s professional game critics. So back into the Oldest House I dove, breathing in the game’s richly strange atmosphere, re-learning how combat works—a violent ballet of unlimited-ammo gunplay leavened with psychokinetic brutality—and completing a main-quest mission. I went to bed feeling a little proud of unsticking myself with this celebrated and significant work of modern media.
My partner, meanwhile, asked me if I was OK. She had heard me muttering out loud the whole time that I played, and detected something dark in my mood. I don’t remember the muttering, but that fact alone isn’t so strange for me. I mutter and grumble in some situations when I’m deeply focused on a stressful task, and I’m not always consciously aware of it. I was grateful for the notice, but assured her that the game didn’t make me feel negative—which was, as far as I knew at the time, completely true.
I picked the game up again hungrily after breakfast the next day, eager to keep working my way through the main story. And, about 24 hours after first returning to Control, I concluded that I need to put it down again, probably permanently. And then I should strike every other game off my to-play list whose primary activities include gunning down hundreds-if-not-thousands of people while completing the core narrative. (Sorry, Red Dead Redemption 2.)
Over the course of the day, you see, my mood sank, and sank. During this time I’d play Control for a while, take a break to do something else while thinking about Control, then return to Control. I was not cognizant of feeling slightly worse after every session with it, despite my steady progress through the story. By the time evening came, I was on-edge and irritable, shaking with undirected anger which seemed to come from no clear source. But you, like my partner, have figured out the source, yes? I came to the realization myself after a quite ordinary texted request from my brother made me growl with rage, as if another goddamned annoyance had been added to the top of a smoldering heap of negativity—of whose presence I only at that moment became aware.
And I knew immediately that it was Control that had buried my heart under a mound of squirming negative input. It tossed on a shovelful of loose dirt every time I gunned down yet another roomful of realistic-looking human beings against a driving drum-and-synth beat, blasting each body until it went down and stopped twitching, all so that I could resume my explorations of the game’s beautiful and mysterious setting. I was so into the wonderful horror-fiction narrative, whose bizarre truths are revealed bit by bit in achingly expert small doses, that I totally disregarded the ever-growing body count for which I was responsible—or what gradual cumulative effect this disregard had on my mood, as I strained to pay as little attention as I could to it.
This is the third time I’ve recognized something like this happening to me, with very similar stimuli, within the last couple of years.
It first happened early last year when my partner and I both became smitten with the gloriously violent multiplayer-cooperative chaos of Helldivers 2. I never took the game quite seriously, playing only easier missions and having a good time accidentally yet repeatedly calling down airstrikes upon my friends and loved ones, and failing upward to a mission-completed screen anyway. But even though the targets are pure fantasy—goopy alien “bugs” and gleaming-metal murderbots—the violence is depicted with cinematic realism as your heavily armed squad methodically seeks and destroys its objectives. And soon I noticed that when I took walks in the real world I started to have visions of all the trees around me burning, all the buildings behind them vanishing in thunderous explosions. This unsettled me. I also noticed that these intrusive visions stopped when I stepped back from the game. I’ve never returned to it.
Months later, some friends invited me to play Valve’s hyper-violent Left 4 Dead 2 with them online. Fifteen years ago, I loved this game. Last year, after a couple of rounds, it left me sick and seething. Something within me had changed in the intervening years. This time, when I stepped away from the game, I found myself experiencing something like the Tetris effect—except instead of seeing falling blocks when I shut my eyes, I saw living flesh being torn apart by gunfire that roared from my own hands, reducing human bodies to quivering meat. And then my bullets carved into the bodies behind them as the first rank fell, and so on after that, because that’s how you play these games; my brain was just idly shadow-boxing the literal experience of play, in order to help me get better at it. And I hated it. I hated these thoughts that put me into the shoes of a mass killer, even a pretend one, drifting up unbidden. I told my friends I couldn’t play Left 4 Dead 2 any more.
Both of these incidents took place over a year ago, so it did take me a day or two to figure out what Control was doing to me. But the truth of it shone like one of the game’s own eldritch beacons as soon as I let myself see it. And… that sucks! I want to keep playing Control! My friends aren’t wrong: it’s a gorgeous video game! But three data points make a triangle, and I simply can’t disregard what it points at any longer, not if I hold my own mental health in any regard.
In this case, I didn’t experience any literal visions. I just felt soul-sick, and got a little bit sicker every time I sighted down my barrel at a security guard’s chest, and then didn’t even bother to watch them flinch and fall as I aimed at the next target. And as soon as my nonsensical reaction to my brother’s text shocked me into considering the possibility, I knew for a fact that letting myself become repetition-numb to innumerable and realistically portrayed acts of mass violence through firearms—no matter how fantastic the setting—just makes me feel awful. Maybe that wasn’t always true for me, but it is now, and I don’t expect it’ll ever change.
An interesting coincidence lets me offer a clarifying counterpoint from Rosewater, another narrative-driven game I happen to be playing through. In the morning of the very same day as my unwelcome Control epiphany, I played through a scene in Rosewater where I tried to talk an ally out of shooting someone else; my companion had the man cornered, and was burning with righteous rage, even as the man begged for mercy. And… it didn’t work! And it felt thrilling and terrible, this one sudden death. My main character became deeply troubled by this turn, making her doubt how she could trust or even understand her companion. The killer picks up on this and also becomes troubled, even though their reasons for the murder remain clear in their heart. I fully expect the single shocking crack of that pistol to continue having reverberations though the story, and my interest and attention is all the more cemented to it from this one act of violence, placed into the narrative with care and intent.
I also appreciate the entirely opposite approach to gun violence employed by Deep Rock Galactic, a cooperative shooter I’ve been enjoying on and off for over a year. The deeply disturbed space-dwarf player characters of Deep Rock are also focused on maintaining their absurd weaponry, with which they defend their mining operations from hordes of enormous and ever-hungry alien insects. But apart from the shooting feeling secondary to the game’s primarily industrial mission goals, the dwarves revel when a fight breaks out, roaring and laughing as bullets smash into chitin, snarling quips like “Die like your mother did!” or “Go lie down forever!” on particularly gruesome hits. Then they all go back to their space rig and spend their wages getting blackout drunk. We are meant to understand that these dwarves are, by modern human standards, not OK. Counterintuitively, game itself overtly acknowledging the absurdity of the violence does something to vent potential trauma before it can accumulate, for me. This game has never given me unwanted visions.
Contrast these games with Control, which seems wholly uninterested in exploring how the player character is psychologically affected by her deputization from civilian life in order to mow down dozens of “corrupted” federal employees per hour, despite suggesting that she does have an active inner life by giving her frequent internal monologues. If the game dropped clues acknowledging her apparent callousness at the relentless bloodshed as another element of the reality-warping setting, then I didn’t catch them within the first dozen hours of play.
Because Control spends no effort on having its characters process the constant violence all around them, the game shunts the task entirely over to me, the only real witness to it all. And I can process it, a little, like I did on Saturday night, the way a light drink in the evening can make you feel good with no hangover. But when I play for hours more, the poisons do start to build up.
I’m not asking for every video game with guns in it to treat them like either Rosewater or Deep Rock do. I’m not asking for any game to change at all. There’s lots of games out there! My list still has so many worthy titles on it even after my new qualifier crosses a few out. I just need to accept, for myself, a disconnect that has developed between my mental stability and games that treat gun violence as breezily as… well, Space Invaders, or the like. Today’s video games still want to include engaging experiences about zapping screenfuls of baddies, and I’m not one to say they should stop. But the expectations for what this experience looks and feels like have changed a lot, and I’ve changed too.
I share all of this because I’m not sure I’ve encountered anyone else with a long history of playing and thinking about video games finding themselves no longer able to play an entire class of games due to its thematic or experiential content. A few months ago I anticipated a future when the oldest lifelong gamers start finding themselves aging out of enjoying the medium due to simple senescence. Maybe my observation in myself today is related to that, somehow. I’m not “worse” at games, compared to how I played them when I was younger. But I am not the same person I was back then, either. Maybe my tolerance for this particular toxin isn’t as high as it used it be. Whatever the reason, I just… I just don’t want to pull the trigger so much, any more.

I’m very much looking forward to Ladytron’s next album, Paradises. It’s due for publication next spring, but the band has been releasing singles from it in a steady drip, and I really like each one. “I See Red” might be the strongest of a strong showing, so far.
The promotional material for Paradises, showing up now and again in my inbox via Bandcamp, is how I first learned that founding member Reuben Wu has permanently—and, by all accounts, amicably—left the band, presumably to pursue his many ongoing art projects. Prior to that, Ladytron’s membership had been a static quartet from its 1999 founding through 2023’s Time’s Arrow. But now there are three: Daniel Hunt, Mira Aroyo, and the amazing Helen Marnie, of whom I’m a double-fan by way of her solo albums from the 2010s.
Promotional graphics for the upcoming album and tour feature the three remaining members. To a long-time fan, these portraits seem unnervingly lopsided or badly cropped at first glance, despite the trio’s very intentional arrangment into various equilaterally triangular formations. This led to behind-the-curve fans like me to ask “Uh, where’d Reuben go?” on the band’s subreddit, and getting the news that way. It’s just something to get used to; time’s arrow, and all that.
The change leads me to reflect on how most album and promotional art for Ladytron has historically either featured all four members, or—at least as often—just the two women. It wouldn’t surprise me if all band portraits from now on always include all three. To feature only Marnie and Aroyo today would look less like “Here’s the band’s main vocalists” and more like “Here’s the whole band (not you, Daniel)”. I wonder if this also means Hunt will contribute more vocals, which I’ve always enjoyed. While absent from any of the band’s hits, Hunt’s voice is prominent in some of my favorite back-catalog songs like “Versus”, and I hear it in at least one of the new album’s tracks, too.
It’s safe to say at this point that I’ve been a fan of Ladytron for longer than I’ve been an attentive fan of any other musical act, even still-active bands I discovered much earlier in life. I like this band a lot and I’m grateful to be present as it evolves and changes over the years, continuously emitting light and magic.

Amy and I plan to march in New York City’s instance of this coming weekend’s No Kings protest. It will be my third march of the year.
Attending means backing out of a professional event I was looking forward to. But after I saw news clips on social media last week with the Speaker of the House describing the upcoming nationwide protest with language like “America-hating” and “terrorist”, I knew I had to go show up for my city and my country again.
The correct response to Republicans widely depicting the coming protests as terrorism is to go out and protest. Each person should get 10 more people to do so. If Republicans are going to hint at state violence in response to legitimate protest, the only answer is bigger numbers.
This resonates with me because, as I write this, the federal government is running a pair of experiments that seem to head towards a common point. First, it’s having the military summarily destroy civilian ships in the Caribbean, baselessly boasting after the fact that they contained terrorists, and daring anyone to stop the government from killing anyone it wants to—though the experimental protocol restricts their targets to non-Americans in open waters, for now. Second, it’s been rolling military units into American cities, ostensibly to assist with domestic law enforcement—entirely at odds with those same units’ trained purpose of repelling foreign armies using lethal force.
These experiments aren’t happening without resistance. Courts have been blocking or at least delaying the full range of military movements that Trump wants. And right now, the brave (and sometimes bravely absurd) people of Chicago and Portland are meeting federal forces every day in the streets, refusing to bend, and letting the masked and cowardly kidnappers of ICE know that real Americans are not afraid of them.
I promised, at the start of the year, that I wouldn’t stand aside and let the thoroughly corrupted and power-gluttonous Trump administration harm my neighbors. By suggesting that the upcoming protests are an act of domestic terror—and by showing the world what they think they can do, with impunity, to anyone they call a terrorist—the Republicans’ words last week have at last directly targeted my city, my streets, my neighbors. And so I have no choice but to join my neighbors on those streets.
In my marches so far, I don’t bring any signs or supplies or prepare in any particular way, other than making sure I’m well rested, fed, caffeinated, and dressed for a long walk outside. I stay relaxed and situationally aware throughout the march. My only goal is to add my body and my presence and my attention to the mass movement, and for a couple of focused hours help remind the usurpers who really runs the place. I always come out of it feeling hopeful and energized, proud to help my neighbors stand strong and visible. It’s the least I can do, and I have to do it.
If you live in the United States, then I invite you to join me. My march starts in Midtown Manhattan at 11 AM on Saturday. You can find the march nearest you at the No Kings site on mobilize.us. You don’t actually need to register there; I don’t bother. You can just show up. That’s the whole of my plan, and it’s worked well for me so far. If it’s your first march, you’ll come out of it feeling charged, and changed. I need to feel that charge again too, and hold it, facing the long winter ahead.

Like millions of others, I purchased the eagerly anticipated video game Hollow Knight: Silksong within a few days of its release. As I write this I’m a short ways into it, just beyond the first of many challenging boss battles, and with many directions to map out and explore. Its design digs deeper into patterns and directions established by the same small creative team’s masterpiece Hollow Knight from 2017. I can already see evidence of design decisions made with eight years of feedback from countless players, in order to emphasize joyful, flowing challenge over mere frustrating difficulty.
I have lived through many such eight-year spans, enough that I no longer take it for granted that my cognitive speed and physical reflexes will meet the challenge of a new work like Silksong. So far, my ability to play more intense video games seems undeteriorated, a fact I meet with relief. Barring an untimely personal end, though, I do expect that this ability will start sliding away from me, someday.
When I reflect on this on a cultural scale, an oddity emerges. People can generally continue to enjoy books, film, and other media for the whole length of their lives, as long as they retain enough faculties to sense and comprehend them. Video games are different. As my cohort continues to age, I anticipate a gradually growing awareness in the larger culture that the first generation surrounded by video games since childhood—the generation as old as the first successful video games—is becoming inexorably locked out of the ability to appreciate them in the same ways that they always had.
I actually don’t feel particularly morbid about this, in part because game makers have shown a more open cognizance of accessibility concerns in recent years. My favorite example is Control, which has layers of thoughtfully designed knobs and sliders that let you tune the game’s difficulty in specific ways. Still, the game all but begs you not to touch them, in order to get the designers’ “intended experience”. But as Gen X trundles through its aging milestones, a half-century after mastering the likes of Pac-Man and Donkey Kong, I expect we’ll see more sometimes-reluctant accessibility layers like this in popular single-player games.
It’s OK for masterworks of media to be challenging, to require long hours of study, practice, and reflection to fully appreciate. That fact is hardly the sole domain of video games. But video games alone seem to be the one major media form which one is all but guaranteed to find more difficult to appreciate, if one lives long enough, no matter how much time and thought one has spent with them. Like my human cohort, video games as a cultural phenomenon are still young enough not to have had to reckon with this fact at scale—but that won’t last forever, and it’ll be interesting when it all starts to change.
“Old spiderweb” by Thor Edvardsen is licensed under CC BY-NC-ND 2.0 .

I enjoy attending indie comix and zine festivals and throwing money around everywhere and bringing home bulging sacks of weird little books that then sit in a growing pile of things I have not read. This is in some ways a worse situation than the traditional and time-honored pursuit of buying ordinary books and not reading them, because at least those look handsome on a bookshelf, spine-out. What to do with my hoard of stapled-and-folded treasures, which turn invisibly anonymous when squeezed onto a shelf amongst their square-bound peers?
A couple of weekends ago I happened upon this solution: Obtain and install a bookshelf scored with a long groove or two, designed less for storage than display. (I’m no woodworker, so I found a Marie Kondo-branded “kid’s bookshelf” at the Container Store, and removed one of its slats.) Choose set of a dozen or so zines from your collection, around any theme or none, and set them on the shelf. Put all your other zines in one or more archival boxes. And then, whenever the mood strikes, rotate out some or all of the books. Maybe share your screenshot on social media every now and then, with shoutouts and links to the creators.
This has worked insofar as I have started reading several books that I obtained a year or more ago. My first setup favored cartoonists who were active on Mastodon. I might very well share more later, as the collection slowly rotates. I’m pretty happy with how this turned out.

Two years ago, I used my then-employer’s nascent LLM-powered chatbot to help me with a personal coding project. It failed, but in a very interesting way. This suggested the potential of generative AI as not a replacement for human work, but an intriguingly novel creative tool that can use unpredictability and even confabulation to help you see your own work from new angles, sparking new insights.
One year ago, I attended a show that shocked me out of a professional crisis, one that very much involved my uncertainty about the explosive growth of LLM-based technology. It spurred me to walk away from a lucrative job with a global tech corporation that had taken a hard turn into a company-wide generative AI embrace. This remains one of the most difficult and meaningful things I’ve ever done, and I have no regrets.
This summer finds me returned to my comfortably pre-FAANG role as a freelancer. And: I have come to use LLM-based technologies nearly every day. I’ve become a paying customer of Anthropic’s Claude. My main client, CodeRabbit, sells an AI code-review service.
To be sure, last year’s exit had far more to do with recognizing how my priorities had diverged from those of my employer, rather than a protest of generative AI specifically. And yet, my personal adoption of the technology feels rather more accelerated than we might have expected at the time, doesn’t it? A fresh examination seems due.
The chatbot as existentialist mirror
I borrow the title of this post from Chats with the Void, a webcomic by the pseudonymous Skullbird about finding personal growth through uncanny encounters with the reflective surface of non-existence. The comic is a long-time favorite of mine and I think of it often, including when I think of what it feels like when I’m having an eerily productive session with an AI chatbot, one that feels connective even though I’m well aware there’s no other mind at all there. Just my own, talking to itself, through this mannequin facilitator.
And that’s my thesis, really: the current state of LLM chatbots, when used with mindful care, help me refine my work by forcing me to organize my thoughts conversationally, and then chat about them with a pseudoexistent entity. For the most part, it reflects my thoughts back at me—but coated with a squirming fuzz of connection and suggestion, picked up after rolling my writing around a unimaginably vast map of stored semantic vectors, trained on sketchily sourced seas of recorded human thought. Reading the chatbot’s replies forces me to regard my own thoughts from new angles, and challenges me to defend my creative choices, or see some areas where I could improve the clarity or completeness of my writing.
When I work with Claude, I bury the poor bot in conversational context. Not only do I feed it all my work, but I’ll pile in any immediately relevant supporting documents, and then wrap the whole thing in a prompt that is often a multi-paragraph screen-filler, laying out the relationship between all this material, my motivations for doing all this work, and the precise sorts of feedback that I hope to get out of the AI. Here are a handful of examples—liberally paraphrased for length—of prompts that I’ve used to launch long conversatins with Claude in the last few months:
Here is a list of assertions about a well-documented technology that I need to write an article about. Are all of these statements technically accurate? Does the whole collection represent the outline of a complete user-level understanding of the technology, or are there some key points missing?
Here is a pitch letter I just wrote to a magazine seeking new submissions, but which I haven’t sent yet. Here is a copy of a page from the magazine’s website about their pitch process, and here’s some more information about this particular call for pitches. Does my letter meet fulfill everything that the magazine’s process asks for? How does the pitch itself read in terms of clarity, flow, and length?
Here is a very long, boilerplate-filled contract that a new client just sent me. Here is a list of the working conditions that my client and I have already informally agreed on. Does this contract support these conditions? If so, show me how. If not, explain why. Beyond that, is there anything in this contract that I might come to regret, if I sign it? You already know what I do for a living and how I prefer working.
Here is the GitHub repository for a static-site generator of my own design. Despite not having worked on it in many years. I did recently start using it to publish a podcast, and it works remarkably well. But it has a significant shortcoming when used for this purpose, and here’s a detailed description of that. What’s a modest modification that I could make to improve this?
Here is a blog post that I wrote, as much for myself as for a public audience, examining my current relationship with rapidly developing LLM-based technology, and how I use AI chatbots like Claude in my day-to-day work. What do you understand the post’s thesis statement to be? Are there any modifications you would make to this draft in order to strengthen this thesis?
All of these have the general form of “Here’s a whole bunch of work I’ve already done. Observe as I salt them with meta-text about my motivations. Let’s crank this through your weights, paired with a question, and see what comes out.” And in every case, I found the output valuable, leading to a back-and-forth of challenges and counter-questions with an infinitely patient semi-entity that gives me sometimes surprising insights and perspectives into my own work, and often points at ways that I could refine it.
This isn’t my only use-case for generative AI, but I think it’s my strongest one. Not a miraculous servant, but a darkly magic mirror.
Unbounded slop versus cognitive middleware
In no case do I ask the chatbot to generate “slop”; there is no step, in my AI-enabled workflows, where I just let the machine operate unbounded, or where I intend its output to be seen by anyone other than myself. In every prompt, I set boundaries, observe the results, and think about what, if anything, they might prompt me to do in response. It is part of a closed system, with me on either end of its function. It is, to use a phrase I bandy about sometimes, cognitive middleware.
Part of why I enjoy the work at CodeRabbit involves the product’s compatibility with my AI philosophy. In that case, CodeRabbit isn’t meant to supplant human code reviewers; it’s something more like a self-powered toolbox that scouts ahead of the human reviewers of any “pull request”—a formal request-for-comment regarding a code modification—attaching a summary and map of its findings, perhaps with some suggestions attached. These are presented tidily and atomically in a single comment, which human developers can heed or ignore, to any degree, at leisure. I legitimately enjoy seeing the bot’s responses to my own documentation pull requests, and more than once it has made apt suggestions for improvements which I interpret and then manually apply. Middleware.
I have experimented with using chatbots much more extensively, giving their leash more slack, and the results haven’t felt as good. In the two years since my first “rubber-ducking” adventures, AI chatbots have become far more apt at prompt-driven software creation. I know this because I do have running, on a private server, a web application that I directed Claude to stack together for me. The result, after a few hours of work, is a complete Python-based application that does what I asked for, to the letter. But it falls short of my own sense of taste in a hundred ways—and I don’t actually know how it works. I don’t like it.
In a recent episode of The Talk Show, Craig Mod—who seems to use generative AI under the same constraints that I do—described how he used Claude to build a web application to fulfill a very specific desire that he had, and was very satisfied with the results. In his case, he spent a couple of weeks on it, working gradually, and staying cognizant of how all of its parts worked, and why. Claude’s job was to help him build and iterate very quickly, far more quickly than he could have done by himself, but never straying from a place where Mod knew how the app worked, and where he should focus his next ideas for improvements.
So why did Mod use a generative AI tool at all, then? Because he knew he’d never have bothered, otherwise! It was a fun project, scratching a personal itch, and there are enough high priority demands on his time that he knew he’d never seriously commit to a solo coding project of great complexity but mild importance and a tiny audience. This resonated with me, and matched my own motivations for that bleak experiment on my server. I want to try it again, with a more expansive and patient attitude.
And so that’s where the summer of 2025 finds me with AI. I have always described my stance towards modern generative AI as “cautious curiosity”, and that hasn’t changed. My characterization from 2023 of the technology as a rubber duckie which can talk back to you remains in place, as well. What has changed over the last year or two is my willingness to explore—mindfully, and with constraints—how this technology can work for me, and help me with the things that I want to do, and make. And there’s something there, even if there’s nothing at all there, and I intend to continue digging. Or, anyway, gazing.
Last month, I wrote:
The Constitution protects Mahmoud Khalil no less than it does me. And if it can’t protect him, then his mistreatment makes me—me personally, and everyone in America I know and love—all of us, it makes all of us suddenly unsafe. For the sake of their own stability and freedom, every American should know that Khalil’s fate is very much bound up in their own.
At the same time, the American government had deported—directly into a brutal El Salvador prison—hundreds of Venezuelan residents of the U.S., with no formal accusation of a crime, and no day in court. I had originally mentioned them in my post about Khalil, but I decided to keep my focus narrow, letting my wrongly imprisoned neighbor stand for the many unsubtle injustices of the new American carceral state. These also include the more recent broad-daylight snatching of Rümeysa Öztürk from the streets of Somerville, where I lived for 14 years, on similar flimsy grounds as Khalil’s detention.
And then it came to light that while none of the abducted men were captured and deported justly, one of them stood out as having the most grossly unjust case, by far: Kilmar Armando Abrego Garcia, a legal resident of Maryland, who suffers in that El Salvador prison even as I write this because American authorities swept him up by accident. U.S. officials admitted as much—and then declined to bring him home anyway. The U.S. Supreme Court, last week, and in a shockingly rare unanimous decision, instructed the government to get a move on with it.
This afternoon, President Trump invited El Salvador’s President Nayib Bukele to the White House. Bukele told the assembled press that he was powerless to release Abrego Garcia from his own country’s prison, while Trump grinned with clear approval.
Bobby Kogan, a senior director of the Center for American Progress, wrote this in response:
You do not have any rights if the government has the ability to send you to prison forever without a trial and there’s literally nothing you can do about it.
This is as fundamentally opposed as possible to what society should look like.
It is your duty as a citizen to oppose this government.
And I’m going to let that speak for me, and help mold my present stance and future actions in defiance of this government. If you live in the U.S., whether you’re a citizen or not, it’s important to me that you take the time to understand the gravity of what’s happening, and that you establish the connections and community and resources that you need in order to best resist it, on a years-long timescale.
Previous post: Assert your way to stronger technical writing



 jmac@jmac.org
jmac@jmac.org @jmac@masto.nyc
@jmac@masto.nyc